Everyone knows that passwords aren’t always secure, annoying to remember and type. Add to that the longer/stronger your password the harder it is to remember. Therefore ssh-keys are very convenient and more secure. However, most people don’t put a passphrase on their ssh-keys because surely this would mean you would have to enter this passphrase every time you use the key and therefore remove the whole convenience of the key.
Ubuntu (and most versions of linux) come with a handy tool (ssh-agent) which can store your passphrase securely and enter it for you when you login. Essentially, this post really is a quick guide to using ssh-agent on Ubuntu.
Here are the commands you need.
1 – Generate a ssh-key
$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/user/.ssh/id_rsa):
Enter passphrase (empty for no passphrase): [Type a passphrase]
Enter same passphrase again: [Type passphrase again]
........
.......
2 – Add the ssh-key to your ssh-agent!
$ ssh-add
Enter passphrase for /home/user/.ssh/id_rsa:
Identity added: /home/user/.ssh/id_rsa (/home/user/.ssh/id_rsa)
3 – Copy the ssh to your remote host
$ssh-copy-id user@remote.com
user@remote.com's password:
.....
4 – Now ssh in… look no passphrase required!
$ ssh user@remote.com
There are also a handy gui tool for adding and removing stored keys. It’s called Seahorse but you can find it by typing “passwords” or “keys” into dash search.
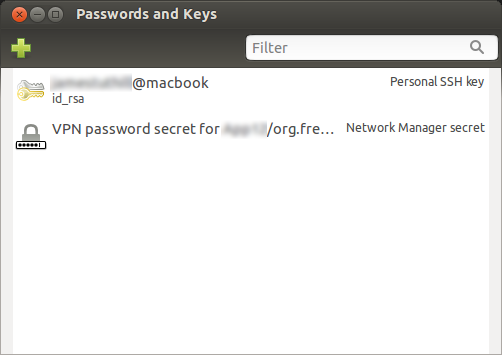
This is a screenshot of Seahorse on Ubuntu.
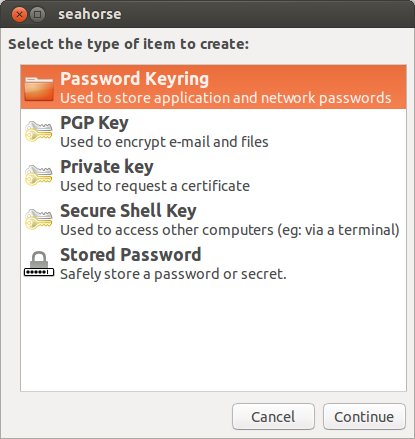
Adding a new key using Seahorse.